Octopus ENTERPRISE
Go further in managing connectivity. Octopus Enterprise allows you to configure advanced identity and device access control options.
In order to orchestrate all the connections that occur in the network, this module interacts with the advanced functionalities of the LAN / WLAN solutions not only intended for guest WiFi, but for any device or identity that connects to the network.
Main Features
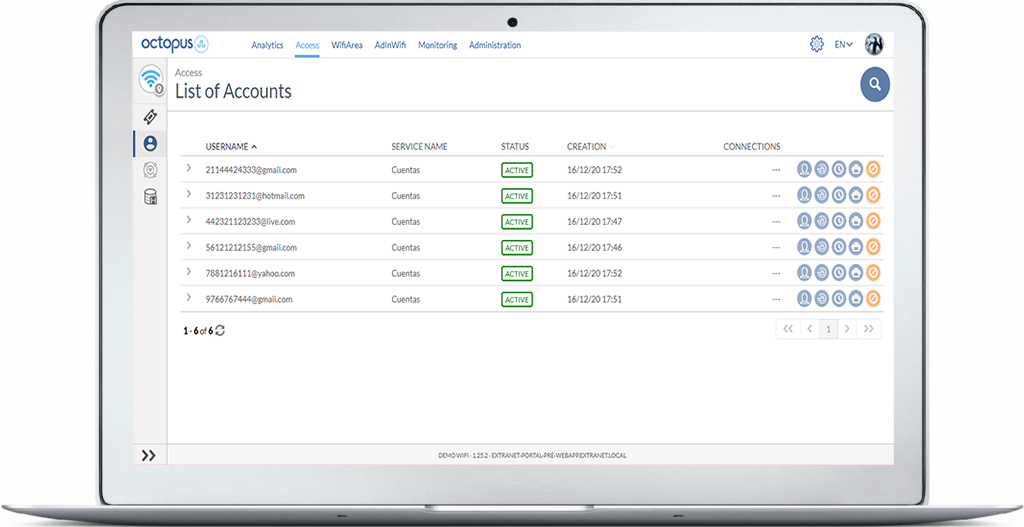
- User accounts administration.
- Integration with identity management tools: Office 365, Google G Suite, Azure AD.
- Mobility or roaming management between venues.
- MAC Caching. After the onboarding process, automatic connectivity for a configurable time.
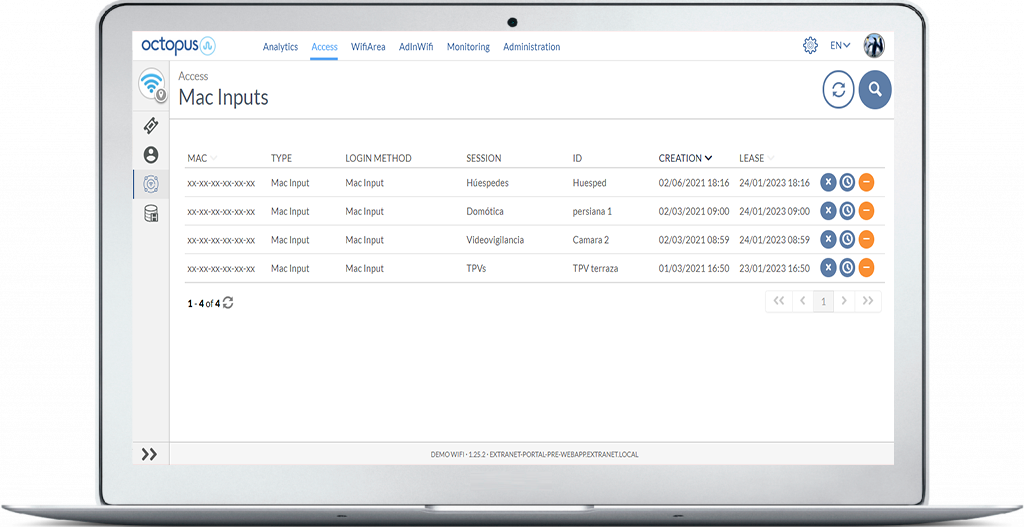
- Device management. Registration of MAC entries for automatic login with the possibility of custom PSK.
- Police Management. Management of access profiles for users and devices
HOW DOES IT WORK?
Previous
Next
- Definition of realms for mobility management between locations.
- Configuration of authentication services for integration with identity management tools.
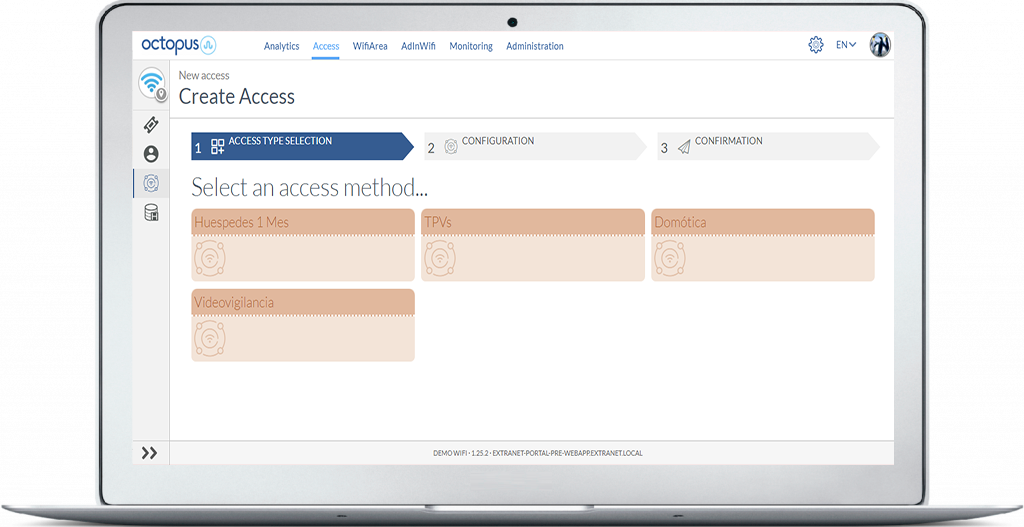
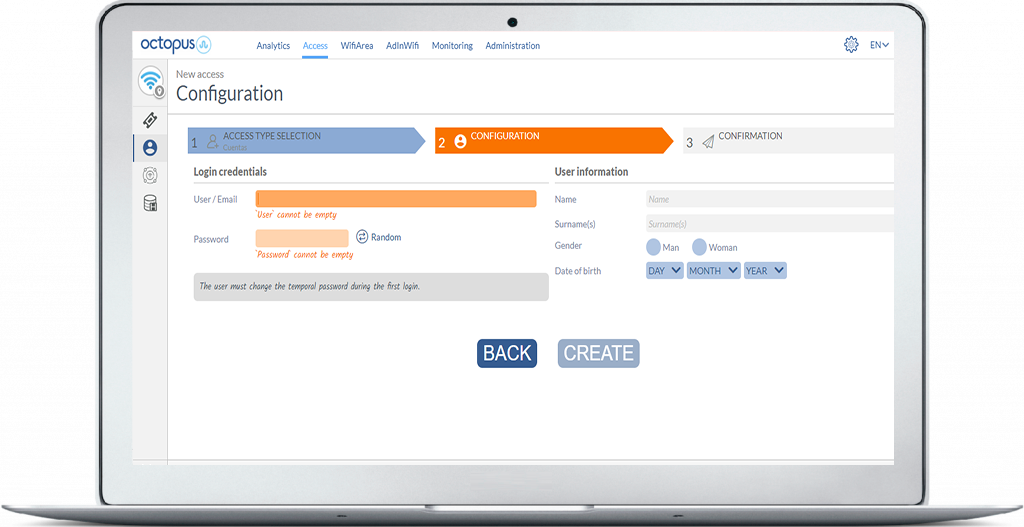
- Management of user accounts with the possibility of issuing them by administrators, user self-registration with and without confirmation and password management.
- MAC Caching: Automatic connectivity to the network for a configurable time.
- Device management: Static MAC inputs for access control and connection monitoring of IoT devices
- Custom PSK: Integration with manufacturers that offer the possibility of custom configurations of PSK keys per device.
- Management of access profiles applicable to devices or identities
PROFITS FOR YOUR BUSINESS
- Orchestrate all the network connectivity elements in a simple and centralized way and independently of the HW.
- Global mobility projects with global user management and roaming between sites through different authentication channels.
- Integrates the service with corporate identity management platforms, for greater access convenience.
- User accounts or identity management on the own platform
- Improved user experience with mac caching without the need to constantly enter credentials.
- Secure connectivity of IoT devices with double authentication factor.